HashiCorp’s licensing switch of Terraform from open-source to Business Source License (BSL) caused a stir in the tech community. Teams were not only concerned about restrictions on commercial use, but also potential lock-in, less flexibility, and how to proceed with infrastructure projects.
Beyond licensing concerns, scaling Terraform brings other issues. When expanding infrastructure, teams often struggle with secure state file storage, module versioning, secret management, and coordinating across multiple environments. Enforcing standards, detecting drift, and maintaining best practices also become more burdensome, especially without strong built-in tools or consistent community support.
OpenTofu was developed as a solution to all this. An open-source fork of Terraform created and maintained by the community, OpenTofu doesn’t just replicate Terraform; it keeps the original concept of openness, enabling developers to build with confidence.
In this article, we’ll explore the key hurdles that arise with Terraform at scale, provide a step-by-step blueprint for migrating to OpenTofu, and explain how modern tools like Quali Torque help manage OpenTofu configurations at scale.
Core challenges of Terraform at scale
Terraform has enabled platform teams to properly and securely manage infrastructure through automation and version control. However, as these teams scale, managing Terraform configurations can introduce new hurdles.
State management complexities
When engineers use Terraform to manage multiple concurrent projects and environments, it becomes complex to manage state files effectively. As your infrastructure expands, storing state files on cloud storage environments often leads to the exposure of sensitive information or to a scenario where access to data is not properly restricted or configured.
Provider and module fragmentation
At scale, using multiple providers or custom modules can lead to version conflicts and several compatibility issues. Engineers can face problems when upstream modules are backward-incompatible. Without consistent versioning, infrastructure deployments become dangerous.
Why IaC alone isn’t enough
While infrastructure-as-code tools bring automation to provisioning, they’re not a complete solution for managing complex infrastructure at scale. Teams must be able to define dependencies and resources to ensure security and compliance.
In an agile environment, DevOps and software development teams sometimes lack the visibility and expertise to know if the right resources have been deployed via an IaC tool. Teams then have to sift through complex infrastructure-as-code every time something breaks to identify what changed, whether the change was intended, and how it affected the system. In other words, troubleshooting is more difficult.
And while IaC tools are valuable for Day 1 operations, Day 2 ops require manual intervention, consuming significant resources and your DevOps team’s time.
Without complementary tools and practices to fill IaC’s gaps, teams will get slowed down by complexity, increasing operational risk. This is why OpenTofu has been such a game-changer, but how can teams achieve a smooth migration?
Step-by-step migration to OpenTofu
The following steps outline how to migrate from Terraform to OpenTofu safely and effectively, while keeping your infrastructure stable and reliable.
Step 1: Pre-migration assessment
Before switching from Terraform to OpenTofu, review your current setup:
- Audit your state files: Know where your Terraform state is stored (like AWS S3) and check how it’s managed.
- Review your project modules and providers: Check which version is being used and ensure they’re compatible with OpenTofu.
Test compatibility: Run OpenTofu in a test environment using the following commands to verify its compatibility with existing code.
opentofu init
opentofu plan
If errors pop up, note the modules or providers causing them.
Step 2: Migrating state files
To safely migrate state files, especially if you’re using a remote backend like AWS S3, you have to be certain that it’s protected and compatible.
Make sure that your backend block in main.tf looks like this:
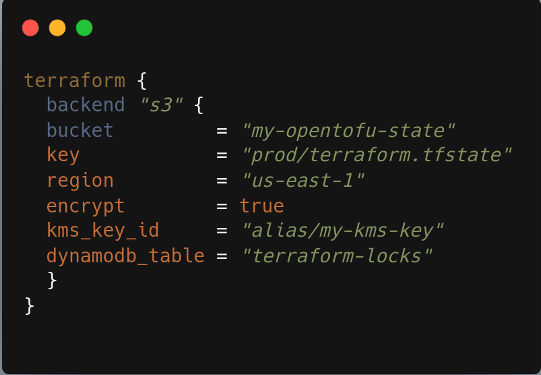
Figure 1: Terraform backend configuration for AWS
Then migrate the state using:
opentofu init -migrate-state
Step 3: Updating configurations
Here, you may need to adjust some of your code for OpenTofu:
- Provider blocks: Check for any provider syntax changes and ensure you’re using versions that support OpenTofu.
- Backward compatibility: Use the following flag to migrate the state and maintain support:
opentofu init -migrate-state
Step 4: CI/CD and team workflows
Finally, you need to update your automation and team processes. Replace Terraform with OpenTofu commands on GitHub Actions or Jenkins. Make sure all team members install OpenTofu!
Also, update your documentation and version control strategies to avoid conflicts (e.g., use tfenv to manage versions across machines).
Advanced OpenTofu configurations
As teams adopt more advanced OpenTofu configurations, managing infrastructure across multiple cloud providers becomes a concern. The following tips will help.
Multi-cloud state management
It’s important to choose and configure the correct backend for state management when using OpenTofu across multiple cloud providers, e.g., AWS, Azure, or GCP.
For AWS S3, teams often use DynamoDB for state locking, while AWS supports encryption with Key Management Service (KMS) and fine-grained identity access management (IAM) control.
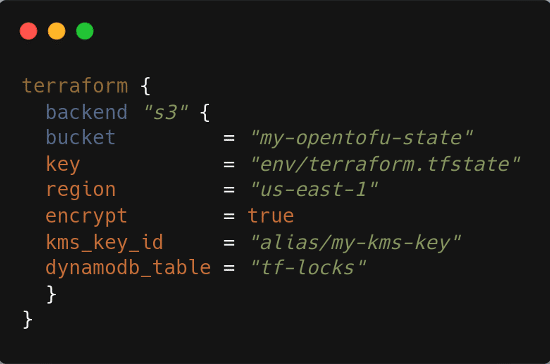
Figure 2: Terraform backend configuration for AWS using S3
For Azure, state management uses a storage account and container with support for state locking via Azure Cosmos DB or Azure blob leases.
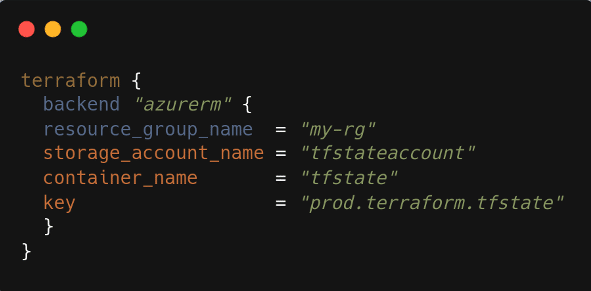
Figure 3: Terraform backend configuration for Azure using Blob Storage
Google Cloud Storage (GCS) uses GCS buckets for state, with built-in object versioning and IAM controls.
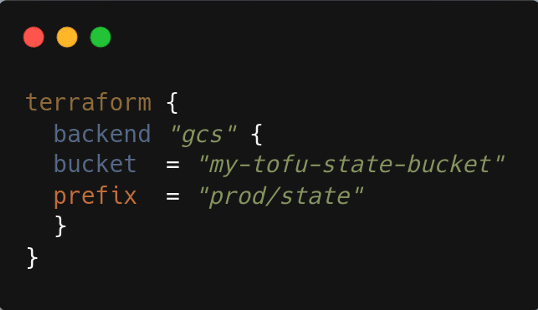
Figure 4: Terraform backend configuration for Google Cloud using Google Cloud Storage
Always make sure you’re using appropriate key management services to encrypt state data at rest and define least privileged access to state files.
Debugging migration issues
While migrating to OpenTofu, you may encounter the following common concerns.
Provider crashes or errors
This can occur if a provider version isn’t fully compatible. Ensure all providers are updated and declared correctly in your configuration.
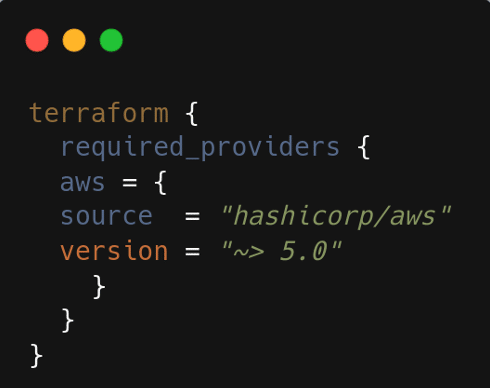
Figure 5: AWS providers for Terraform
State file mismatches
If the OpenTofu plan displays unexpected changes, it may indicate that the state file didn’t migrate properly. If this occurs, run:
opentofu init -migrate-state
Next, go back and inspect the .terraform folders or backend files.
Unsupported flags or syntax
If your config uses deprecated Terraform-specific flags, check OpenTofu’s release notes for updated syntax or migration paths.
Key criteria for a successful migration
Achieving a successful migration to OpenTofu requires careful planning and alignment with best practices. Below are some key criteria to keep in mind.
Backward compatibility testing
One key strength of OpenTofu is its ability to work with most existing Terraform codebases. OpenTofu is a fork of Terraform, so even though Terraform modules and providers work out of the box, you should test any custom or heavily versioned modules.
Before starting, set up a sandbox environment for backward compatibility testing using the following commands:
opentofu init
opentofu plan
Next, confirm the output with Terraform to ensure that there’s no unexpected behavior.
Unified workflow integration
To enforce standards during and after migration, integrate OpenTofu with your existing DevSecOps workflow:
- Security scanning: Integrate tools like Checkov, tfsec, or Open Policy Agent to validate your security posture via policy format checks and linting.
- CI/CD pipelines: Update your workflows in GitHub Actions, GitLab CI, or Jenkins to replace Terraform commands with Open Tofu equivalents.
Monitoring and validation
Once the migration is complete, run opentofu plan regularly in CI to detect any changes and catch potential drifts. Also, utilize tools or custom scripts to identify when the infrastructure deviates from the state file.
Monitoring backend logs to track state access and detect unauthorized changes is key. Migration is not just about moving code; it’s about maintaining the same level of stability, security, and visibility across your entire infrastructure.
Pitfalls to avoid in a failed migration
Avoiding a failed transition to OpenTofu means being aware of common mistakes that can disrupt the process or compromise your infrastructure.
Ignoring state file dependencies
Teams commonly fail to understand how tightly coupled the state files are to the modules and cloud resources. If some environments are migrated to OpenTofu while others remain on Terraform, you risk state file corruption or breakages in shared modules.
Solution: Perform an audit of your state before proceeding, then migrate all dependent modules and environments together to prevent any overlap.
Overlooking team training
When teams are unfamiliar with OpenTofu syntax or behaviors, they may unknowingly introduce errors. OpenTofu can also introduce new CLI flags or community-driven enhancements that are not present in Terraform.
Solution: Provide internal documentation on how to install and configure OpenTofu, descriptions of the major and minor differences from Terraform, and updated workflows for init, plan, apply, and CI/CD operations.
Underestimating multi-cloud complexity
State management is more complex in hybrid environments. Cloud providers have different storage and locking mechanisms, and failing to plan for this can result in the desynchronization of state files and inconsistent locking.
Say you uses AWS for production and GCP for development and tries to migrate only the GCP environments to OpenTofu. You’ll end up with backend incompatibilities and inconsistent state access patterns, causing drift and failed deployments.
Solution: Standardize your backend configurations across clouds and test locking encryption before rollout.
Managing OpenTofu at scale with Quali Torque
When DevOps Teams migrate their entire infrastructural components to OpenTofu, a few operational hurdles are bound to pop up:
- State file collisions ➡️Leads to errors and extra work: When multiple team members work on the same infrastructure, they can accidentally overwrite or corrupt the OpenTofu state file if state locking isn’t managed adequately
- Poor cost visibility ➡️Results in unexpected budget overruns: DevOps Engineers may end up provisioning expensive resources without fully understanding the cost implications.
- Manual security and compliance checks ➡️ Slows down deployments and increases risk: Performing these checks by hand is time-consuming and can lead to human error.
How Quali Torque enhances OpenTofu workflows
Quali Torque addresses the above issues by adding automation, visibility, and governance to OpenTofu workflows. This enables faster, safer, and more efficient infrastructure management at scale via the following services.
Environment as a service (EaaS)
Torque makes it easy to spin up and test OpenTofu environments on demand. This is ideal for testing, development, or debugging without affecting production or shared state.
With Quali Torque, infrastructure engineers can:
- Launch OpenTofu environments with a single click or API call
- Preserve and reuse state between sessions for troubleshooting
- Reduce cloud sprawl by automatically cleaning up unused environments
Environment as code (EaC)
Quali Torque comes with an out-of-the-box workflow to automate actions, allowing you to launch, monitor, and maintain all your environments as code, including infrastructure, services, and dependencies. The platform lets users treat OpenTofu as a component within an environment, removing the need to manage modules separately.
With Torque’s native UI and GitOps integrations, teams can launch, monitor, and maintain full-stack environments, bringing consistent automation to complex deployments.
Governance automation
Quali Torque enables policy enforcement in the pipeline without slowing teams down. You can enforce tagging standards, cost thresholds, and security rules across multiple environments and generate audit-ready compliance reports to satisfy internal and external regulatory needs.
Developer self-service
Platform teams can offer a catalogue of reusable OpenTofu modules that developers can deploy without waiting on apps. This allows you to control access via role-based access control (RBAC) so that only people with the proper permissions can manage a given environment. Torque even provides curated, standardized templates to maintain standardization and reduce misconfigurations.
Operational visibility
With the platform’s real-time visibility, you can easily see into your infrastructure and activity, including resource relationships and dependencies, eliminating bottlenecks caused by connections or risks.
Support for Day-2 actions
Quali Torque helps to improve performance by automating critical Day-2 operations on your live infrastructure and environments. Whenever an anomaly occurs, indicating a potential violation of your custom infrastructure policies, it notifies your teams and ensures there is adequate remediation.
Conclusion
Moving to OpenTofu is a smart business and technical decision because it lets developers future-proof their infrastructure provisioning, avoid licensing bottlenecks, and support open-source initiatives. Plus, it comes with backward compatibility, making it suitable for enterprise use.
By combining OpenTofu with tools like Quali Torque, platform teams can enable automation, enforce policies, improve visibility, and move faster without having to deal with control or security configurations.
To learn more about how Torque enhances OpenTofu, visit the Quali OpenTofu page, or explore our infrastructure as code tools and support for IaC solutions, including OpenTofu, Terraform, CloudFormation, Helm, and Ansible.

