As Infrastructure as Code (IaC) automates the management of cloud resources, it introduces the need for robust governance to prevent misconfigurations, security vulnerabilities, and compliance breaches.
Effective cloud governance for infrastructure defined via OpenTofu requires not only establishing policies standards IaC, but also enforcing them to ensure that all infrastructure deployments and changes are traceable, auditable, and aligned with organizational goals.
Governance is also critical to optimize costs by enforcing resource usage policies, optimizing resource allocation, and preventing over-sized and unnecessary cloud resources.
By automating compliance with governance policies for OpenTofu, cloud governance reduces the risk of human error and enhances overall security posture. Ultimately, cloud governance enables teams to leverage the benefits of IaC while maintaining control and ensuring operational excellence.
Here we’ll explain how to provision infrastructure defined via OpenTofu in a way that enables automated enforcement of cloud governance policies.
Step 1. Establish a developer platform to provision your OpenTofu IaC
On their own, IaC tools like OpenTofu lack the monitoring capabilities needed to identify when cloud resources violate cloud governance policies.
Enforcing governance for OpenTofu requires establishing a platform from which your teams can provision infrastructure, which enables automated monitoring and the ability to deny activity based on those policies.
This has the added benefit of broadening access to provision infrastructure. Using a platform engineering approach to provision infrastructure allows DevOps to simplifying provisioning in a way that reduces the need for expertise in OpenTofu or public cloud platforms just to run the infrastructure.
To begin, add the public URL of the git repository that contains your OpenTofu modules to your Quali Torque account. The platform will identify all your IaC modules and create new YAML files in the platform with the necessary resource configurations.
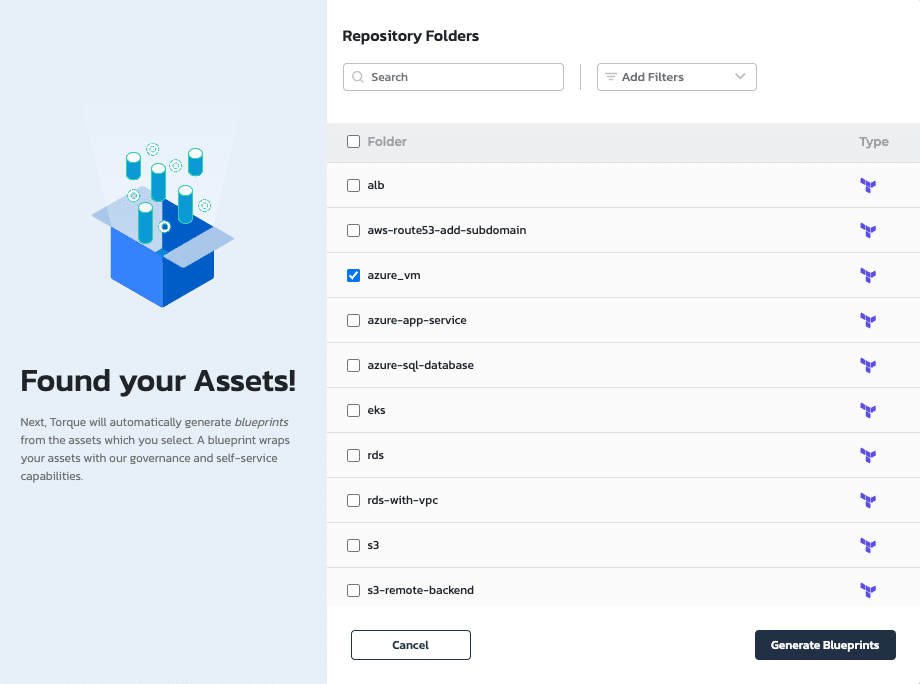
Quali Torque identifies the Terraform, OpenTofu, and other IaC modules in your Git repositories.
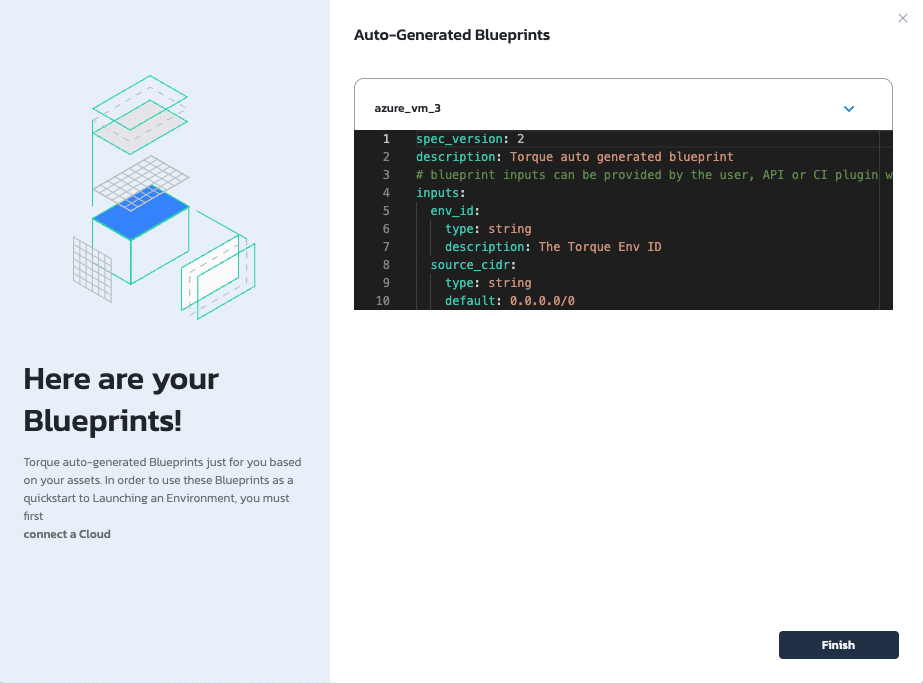
Torque automatically generates a YAML leveraging your Terraform configuration so you can provision via Torque.
This has two benefits:
- Provision individual resource defined via OpenTofu via Torque’s self-service catalog: All users can browse, search, and filter the resources in Torque’s self-service catalog, then provision each one by simply clicking “Launch.” Torque administrators can set default values for parameters, authenticates all cloud accounts centrally, and enforces role-based permissions so end users can’t modify configurations for the resources in the catalog. This enables IaC experts to democratize access to provision infrastructure defined in OpenTofu regardless of their teammates’ expertise with the product or access to security credentials.
- Create and provision complete application environments leveraging OpenTofu and other IaC resources: Torque admins can also find all their OpenTofu resources in the Designer Canvas, where they can search and add them to start orchestrating an application environment. Based on the resources, dependencies (which are set using the Designer Canvas’s visual UI), and parameters, Torque generates a separate YAML platform defining the plan to generate the environment. This YAML can also be listed on the self-service catalog, where users can provision it on-demand.
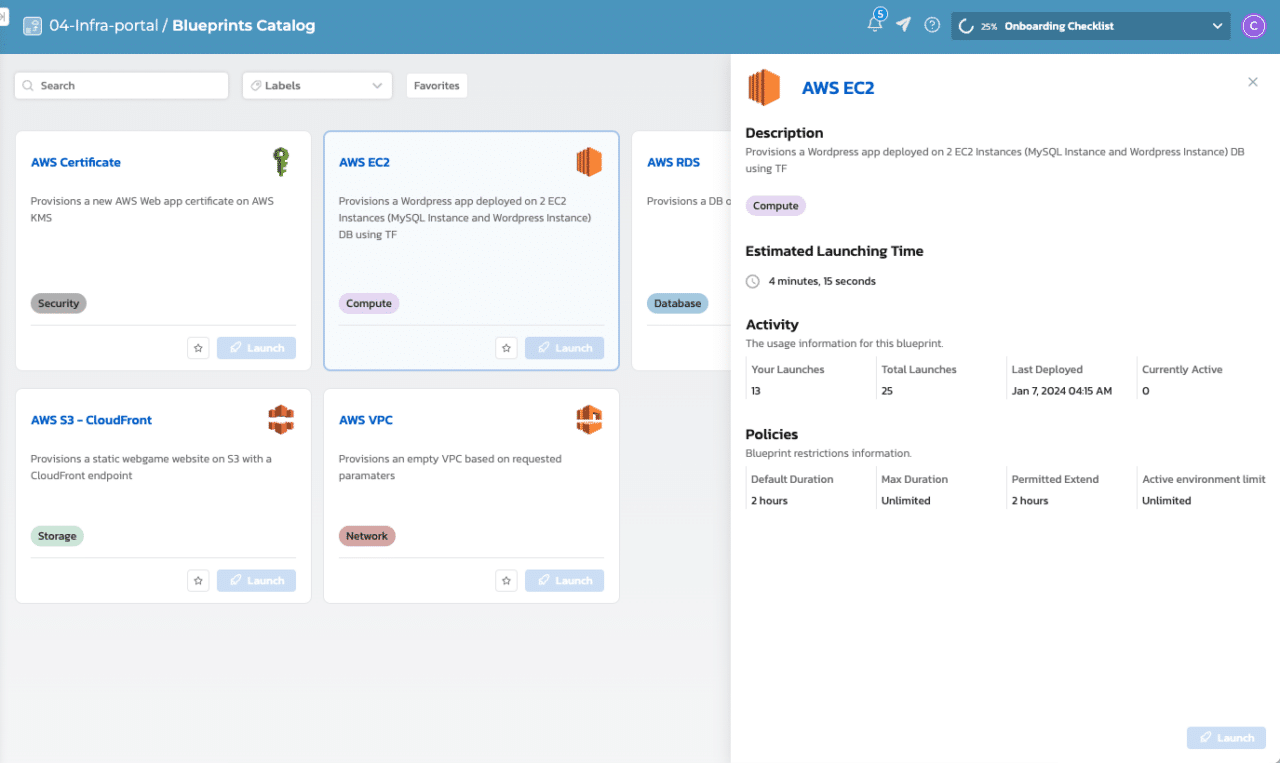
Here is a sample catalog showing self-service provisioning of environments via Quali Torque.
To learn more about no-code environment orchestration with Quali Torque, watch this brief demo video:

Once you’ve established Quali Torque as the platform from which your teams provision their environments, you can set cloud governance policies to ensure all infrastructure adheres to your standards.
Step 2. Set and enforce your custom cloud governance policies
Torque continuously monitors all cloud resources provisioned via the platform, which enables it to recognize and react to specific details regarding those resources.
In the Governance menu in their Torque account, administrators can find Policies. Here admins can set and enforce specific rules for how their teams use infrastructure defined in OpenTofu, Terraform, or other IaC tools.
While Torque allows custom policies, the platform also comes with basic policies based on the Open Policy Agent (OPA) standard, which admins can configure and apply immediately upon creating an account.
In the example shown below, an admin has set a policy for allowed Azure VM sizes. This kind of policy can have a significant impact on cloud cost optimization by prohibiting DevOps teams from running VMs that are larger—and therefore more expensive—than needed to support their workloads.
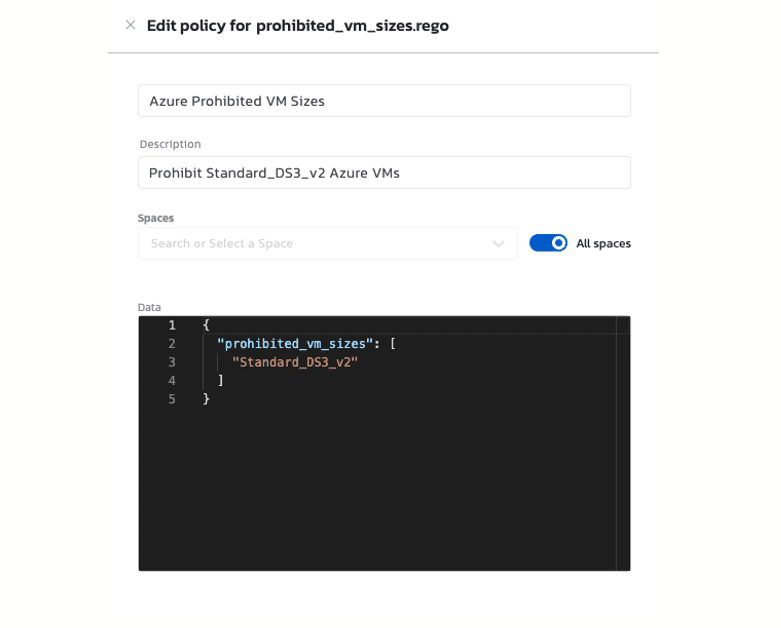
With this policy activated, any attempt to launch an environment containing any other Azure VM size will be denied automatically.
Other popular examples include:
- Allowed cloud providers
- Prohibited public cloud storage configurations
- Maximum runtimes for environments
- Maximum expected cloud cost (based on Torque’s calculation of cloud resource and pre-set environment runtime)
Admins can choose to enforce these policies to all users in their Torque account or only to specific groups of users.
Approval workflows also allow users to see the individuals responsible for approving their requests and the status of their requests for approval.
To learn more about cloud governance using Quali Torque, check out this brief demo video: