Infrastructure as Code (IaC) tools have fundamentally changed how engineering teams build, scale, and manage their cloud environments. Instead of manually configuring servers and services, teams codify infrastructure into reusable templates, making deployments faster, repeatable, and consistent.
Of all the Infrastructure as Code tools available today, one has been at the heart of this movement: Terraform. Yet for many developers, working with Terraform directly can be intimidating. Between learning cloud platforms, security best practices, and Terraform syntax itself, deploying infrastructure often becomes a complex, risky task.
Worse, the traditional approach forces developers to rely heavily on DevOps teams, leading to bottlenecks, long wait times, and frustrated teams on both sides.
The solution? Self-service Terraform, which is designed to put safe, governed, and automated infrastructure directly into developers’ hands without exposing them to unnecessary complexity or risk.
In this article, we’ll explore why traditional Terraform usage falls short, what self-service Terraform looks like, and how modern tools such as Quali Torque can help make it a reality for your teams.
Common challenges for Terraform self-service
While Terraform is a powerful tool for managing cloud infrastructure, it wasn’t built with day-to-day developers in mind. For many teams, getting from an idea to a working resource in the cloud means navigating a steep learning curve, security hurdles, and a lot of operational overhead.
Complexity creates friction. Using Terraform isn’t just about writing a few lines of configuration. Developers often have to understand:
- Cloud provider architectures (AWS, Azure, GCP)
- Network security (VPCs, subnets, firewall rules)
- Identity and Access Management (IAM)
- Secrets handling and state management
For teams focused on building features, not infrastructure, Terraform’s learning curve can be a hurdle. Any mistakes made along the way will be costly.
Risky security practices. Traditional Terraform workflows often require developers to have access to sensitive cloud credentials. This model:
- Violates least-privilege principles
- Makes auditing more difficult
- Comes with a higher risk for code misconfigurations that create security vulnerabilities
Operational bottlenecks. Without a self-service option, every infrastructure request becomes a ticket that the DevOps team needs to handle manually. Spinning up a database, creating a new VPC, or setting up a testing environment—it all stacks up quickly. DevOps teams become a bottleneck, and developers are stuck waiting instead of coding. Nobody’s happy, and delivery timelines start to slip.
Pipeline and local development challenges. Trying to bolt Terraform into an existing CI/CD pipeline isn’t always straightforward. Developers often have to set up Terraform locally, deal with state management, and figure out how to make everything work nicely with the pipeline. Small misconfigurations can cause big headaches, and debugging those issues wastes even more time. It adds friction to the developer experience instead of making things easier.
Terraform lacks context visibility. DevOps and engineering teams often don’t have a clear view of what infrastructure was deployed with Infrastructure as Code tools or who made the changes. When something breaks or drifts out of configuration, they’re stuck digging through tons of code and logs to find the problem, slowing down the CI/CD pipeline. Most companies already track app performance and code quality closely, but that same visibility is needed for infrastructure, too. Without it, maintaining speed, security, and governance across the delivery process becomes a real challenge.
What is self-service Terraform (and why does it matter)?
Self-service Terraform means giving developers the ability to deploy cloud infrastructure themselves—safely, securely, and within organizational guardrails—without requiring deep Terraform or cloud expertise.
Instead of handing developers a raw Terraform repo and some cloud credentials, self-service platforms abstract away complexity. Developers select what they need from a catalog of pre-approved infrastructure blueprints, fill in a few variables, and launch—all without ever touching sensitive configurations or Terraform internals.
Benefits of self-service Terraform include:
- Developer autonomy: Developers can launch environments, services, or applications when they need them, without filing tickets or waiting for approvals
- Built-in Security and Governance: Access controls, policies, and compliance checks are integrated into the platform, ensuring security without slowing down innovation
- Faster Time-to-Value: Infrastructure provisioning shrinks from days (or weeks) to minutes, unlocking faster feature development, testing, and releases
- DevOps Efficiency: DevOps and platform teams can focus on high-value work such as optimization, automation, and scaling, instead of serving as a manual provisioning help desk
Key components of a self-service Terraform platform
Building a self-service Terraform platform isn’t just about making life easier for developers—it’s also about making sure infrastructure stays secure, consistent, and scalable.
Here’s what a strong platform needs to have:
Predefined infrastructure modules
Instead of asking developers to write Terraform code from scratch, you can offer ready-to-go modules for common use cases, such as databases, load balancers, and Kubernetes clusters. These self-service modules hide all the messy details behind simple inputs, so developers can quickly provision what they need without worrying about breaking anything. It’s all about balancing flexibility with guardrails—developers still get options, but the core setup stays consistent and secure.
Role-based access control (RBAC)
A good self-service platform should enforce fine-grained permissions, so developers only have access to the resources they actually need. This keeps your environments safer and helps avoid accidents such as someone accidentally nuking production resources. Plus, it makes audits and aligning with compliance goals much easier when you can see exactly who has access to what.
Secure secrets management
Passing around cloud credentials or API keys manually is a recipe for trouble. A self-service setup should handle authentication and secrets behind the scenes, keeping sensitive data out of reach from users who don’t need to see it. Developers can authenticate once, and the platform takes care of securely injecting any needed credentials into the provisioning process. Less manual handling means fewer security risks and fewer mistakes.
Approval & governance workflows
Even with self-service, there still needs to be a safety net. Certain infrastructure requests might require approvals or extra checks. A good system will automatically route these requests through lightweight approval workflows without slowing everything down. Developers stay productive as long as they’re infrastructure is compliant, while operations teams stay confident that governance and security policies aren’t being skipped.
CI/CD integration
If deploying infrastructure feels separate from your normal coding and shipping workflow, that’s a problem. A strong self-service platform plugs directly into your CI/CD pipelines, making infrastructure changes just another part of your build and deploy process. Developers can trigger infrastructure provisioning through pull requests, pipeline runs, or automated actions—no need to jump between tools or set up local environments.
Developer experience
When all is said and done, the platform should feel effortless for developers. They shouldn’t have to know the ins and outs of Terraform, cloud providers, or networking just to spin up a testing environment. Whether it’s through a simple UI, API calls, or command-line tools, the experience should be fast, intuitive, and closely aligned with how developers already work. The less friction, the faster they can move.
Best practices for rolling out self-service Terraform
Rolling out a self-service Terraform platform isn’t just about setting up the tool—it’s about making sure everyone gets the most out of it while keeping things secure and manageable.
Here are some best practices to follow when rolling it out:
Clearly define ownership and permissions
Before jumping into the platform, it’s crucial to define who owns what. You want to make sure that every team or individual has clear permissions around what resources they can provision and manage. It’s not just about who can do what; it’s about making sure you’re not giving anyone too much access by accident.
Provide solid documentation and onboarding
Developers shouldn’t have to guess how to use the platform. A good documentation portal and clear onboarding materials are key to making the adoption process smoother. Include step-by-step guides, FAQs, and troubleshooting tips. The easier it is for developers to get up to speed, the quicker they’ll start using the platform without hesitation.
Regularly review and update templates
The cloud landscape changes fast, and so should your Terraform templates. You’ll want to review and update your predefined modules and templates on a regular basis. This ensures they’re always secure, cost-effective, and efficient. A template that worked well six months ago may not be the best solution today, so keep an eye on evolving best practices.
Monitor usage and gather feedback
Once the platform is live, it’s important to keep track of how it’s being used. Are developers making a lot of requests for certain resources? Are there pain points or bottlenecks? Gathering feedback from your teams can help you spot areas that need improvement.
Focus on continuous improvement
A self-service platform isn’t a “set it and forget it” kind of tool. It needs to be continuously improved based on feedback, changing security requirements, and evolving team needs. Keep an open line of communication with your developers, and always be on the lookout for ways to streamline processes, improve security, or add new features that make the platform even more valuable.
How to implement self-service Terraform with Quali Torque
Quali Torque helps automate and manage infrastructure with Terraform while keeping it secure and simple for developers. It provides a self-service platform where teams can quickly provision environments, reducing friction and letting developers do what they need to do the most instead of dealing with the fine details of infrastructure management..
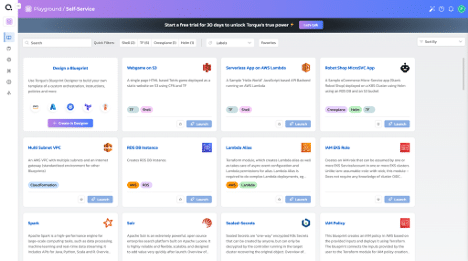
Quali Torque’s self-service catalog makes it easy to find and launch Infrastructure as Code and environments.
Quali Torque simplifies infrastructure management by centralizing secrets, so developers never have to handle sensitive information directly. It democratizes access through role-based access control (RBAC), ensuring that users only have the necessary permissions to provision resources. Torque streamlines provisioning by automating complex details, making it easy for users to deploy environments without worrying about underlying configurations. It enforces governance by automatically denying provisioning for any resource that doesn’t comply with defined policies. Finally, Torque provides comprehensive visibility, allowing DevOps and admins to track resource usage and proactively resolve any errors or discrepancies that arise.
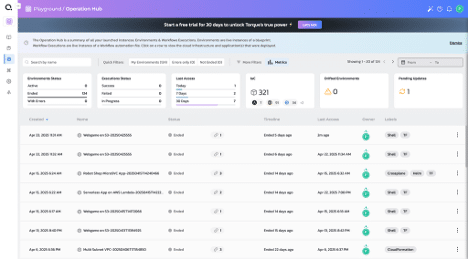
Quali Torque’s Operation Hub shows which resources have been provisioned recently so users can understand how IaC is being used.
Let’s take a look at some of the features that help you implement self-service Terraform with Quali Torque.
Build a service catalog
Start by creating a curated catalog of blueprints inside Torque, aligned with your organization’s needs. Common services might include:
- Development and test environments
- Database provisioning
- Kubernetes clusters
- Serverless app frameworks
Each blueprint defines the infrastructure, guardrails, and variables developers can customize.
Automate infrastructure requests
With Torque, developers don’t need to touch Terraform at all. They can:
- Use a simple UI to select and launch resources
- Call APIs to integrate infrastructure provisioning into applications or pipelines
- Trigger environment creation based on pull requests or GitHub actions
No Terraform knowledge, no credential exposure—just outcomes.
Enforce policies as code
Torque lets you embed policies directly into blueprints or deployment workflows. Whether it’s cost controls, resource limits, or security rules, policies enforce compliance automatically, without slowing developers down.
Federated identity and access
By integrating Torque with your single sign-on (SSO) solution, you centralize access management, ensuring the right people have the right permissions without adding manual processes.
Self-service Terraform: The takeaway
Self-service Terraform isn’t just a “nice-to-have” anymore—it’s a critical enabler for modern, agile engineering teams. Developers get the autonomy they need to move fast. DevOps and platform teams regain the bandwidth to innovate instead of serving as manual gatekeepers. Security and governance are baked in, not bolted on.
Quali Torque makes this future possible today. By combining the power of Terraform with a self-service experience that’s secure, scalable, and compliant, Torque empowers your teams to deliver better software, faster, without sacrificing control.
Ready to give your developers the infrastructure freedom they need — safely and at scale?
Book a demo and get started with Quali Torque today.

