Welcome to this month’s roundup of product enhancements for Quali Torque.
If you’re not familiar, Torque is a platform engineering tool that accelerates and simplifies the design, provisioning, and launch of cloud environments for use cases like software development, QA and testing, software demos, and others.
To see our latest product updates in action and submit questions about Torque to our team, join our next Torque Talk webinar session on Wednesday, May 1st: Torque Talks: Optimizing cloud governance through platform engineering
Here are this month’s updates:
OpenTofu Support for Environments
Since HashiCorp announced changes to Terraform licensing last year, our users have asked how Quali will address it.
OpenTofu is a fork of Terraform that is open-source, community-driven, and managed by the Linux Foundation. Our new update means that users who choose to use OpenTofu can create blueprints in Torque that incorporate those resources alongside others defined in Terraform and other IaC tools.
Through this platform engineering approach, DevOps teams can reduce manual orchestration with reusable templates for environments consisting of resources defined across various IaC tools, then enable developers to provision them with just a few clicks via Torque’s self-service catalog.
Since OpenTofu is fully compatible with Terraform, Torque provides the same functionality that it provides for Terraform, including policies, updates, drift detection, auto-tagging, pre-post scripts and more.
Reference a Binary File for Terraform (including Versions Beyond 1.5.5)
For users that have embraced Terraform versions beyond 1.5.5, which fall under HashiCorp’s Business Source License and are therefore not open source, Torque can reference a binary file instead of the version in the Terraform grain created in the platform.
Torque will not perform any validation on the binary and is effectively unable to understand what the binary contains. This means that Torque administrators can leverage all versions of Terraform when creating environment blueprints going forward.
Since Torque allows Terraform users to create and provision reusable templates for their environments—including all the infrastructure and application services—this update should help Terraform users continue running their complex environments even as they navigate the nuances of open source licensing between HashiCorp and OpenTofu.
Prefix CloudFormation Stacks
Customers using CloudFormation can now prefix all stacks they create via Torque with a customized prefix to adhere to their organization’s standards. There are several ways to do it:
- Define a system param
- Define it in the blueprint
Defining a system param means creating an account-level or space-level parameter with the predefined name SYSTEM_CFN_STACK_NAME_PREFIX and the string you wish to use as a prefix as value.
Using this system param means that the prefix will be applied to all CFN stacks that are created by Torque in the entire account (if it’s in the account level) or in the Space (if it’s Space-level).
Customizable Announcements and Maintenance Mode
When account admins need to share information regarding the blueprints that their users can access in the catalog, Torque can now help to get the word out and protect blueprints when needed.
Announcements allow account admins to publish messages to account members in all or part of a Space. The announcements will show as a banner on the top of the Space pages:
Maintenance mode, meanwhile, will disable all catalog items and provide a message to any user who tries to access them. This allows admins to lock down catalog items and push updates to blueprints, policies, workflows, or other account settings before any users launches an environment.
Seamless Launch for “Always On” Environments
Previously, when provisioning environments via Torque, the platform did not differentiate between ephemeral environments which require a duration to automate teardown and “always on” environments like those used for production, which would not be terminated.
Our new update provides an option to select “Always On,” which removes the duration field for users so they can continue through the deployment process seamlessly.
For space developers, the duration policies section clearly distinguishes between Ephemeral and Always-On durations, ensuring that only relevant fields are displayed for selection.
Space-Level Credentials
Credentials are an important aspect of Torque and help keep things tidy and secure.
Space-level credentials allow administrators to override the credentials defined per the entire account with values that apply only to a specific space. This capability is critical in cases where a certain sensitive parameter needs a specific value.
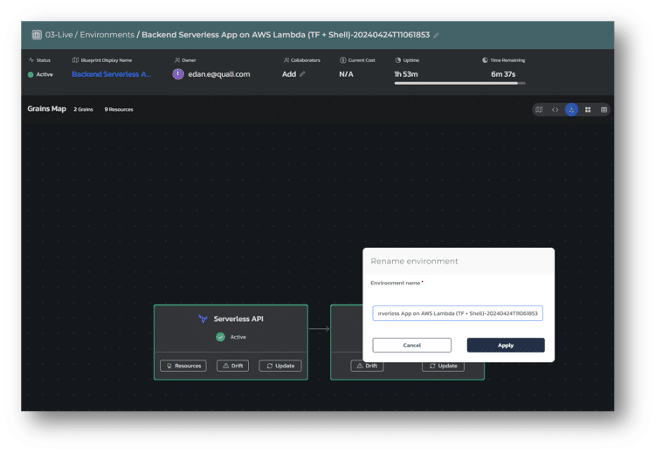
Renaming Live Environments
In response to a common request among our users, we’ve introduced the ability to change the name of a live environment. This allows further customization to align with your specific use cases.
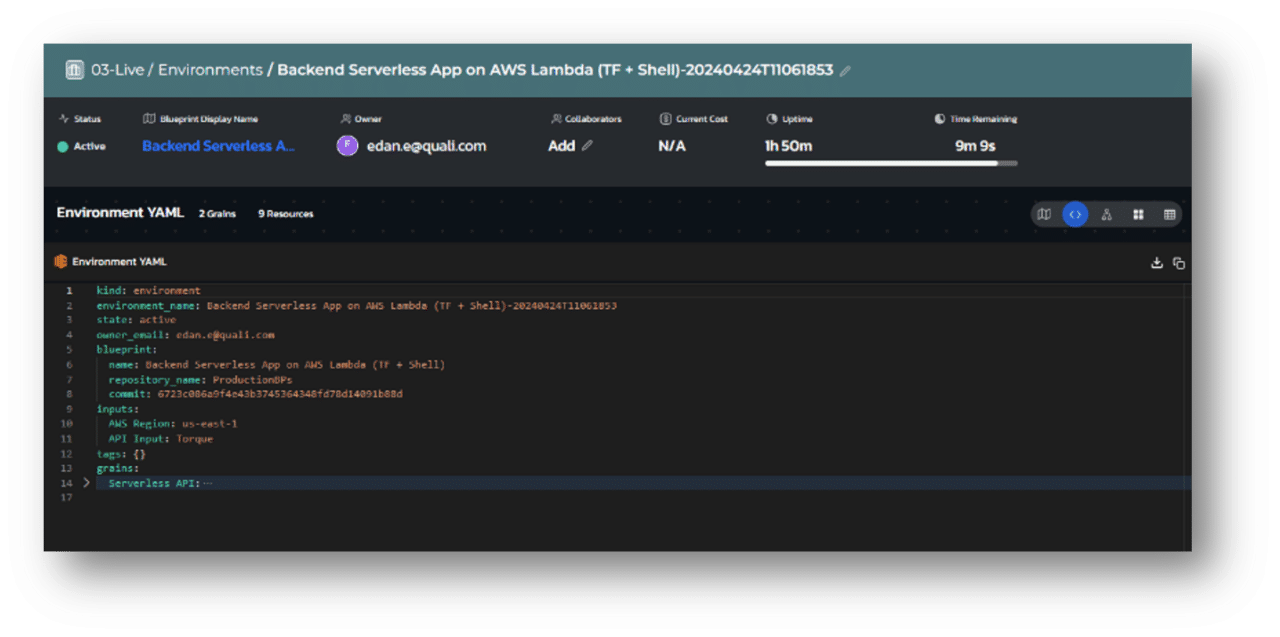
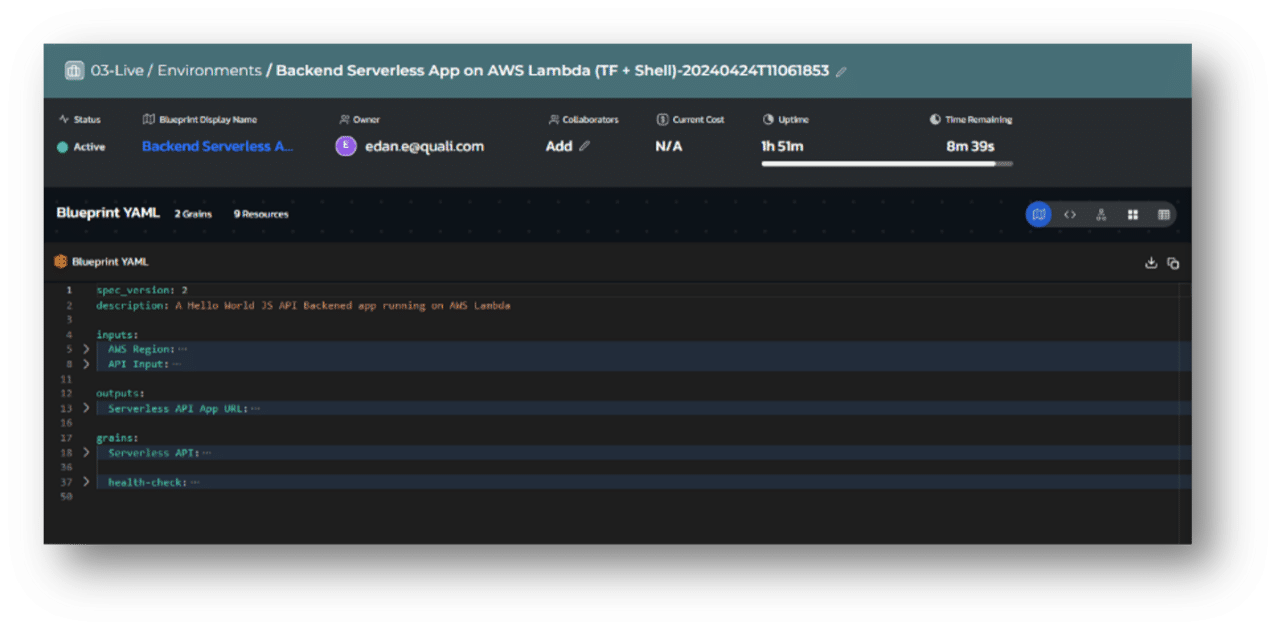
View Environment Blueprint YAML and Environment YAML for Live Environments
The various stakeholders who need to access a live environment often need different information about that environment.
Our latest update accommodates these needs with multiple options to view the code for the blueprint and environment.
When viewing a live environment, users can view the Blueprint YAML from which the environment originated, as well as the Environment YAML which defines the exact deployment of the specific environment. This can be valuable for those who want to take a GitOps approach and use their Environments as Code.