Platform Engineering
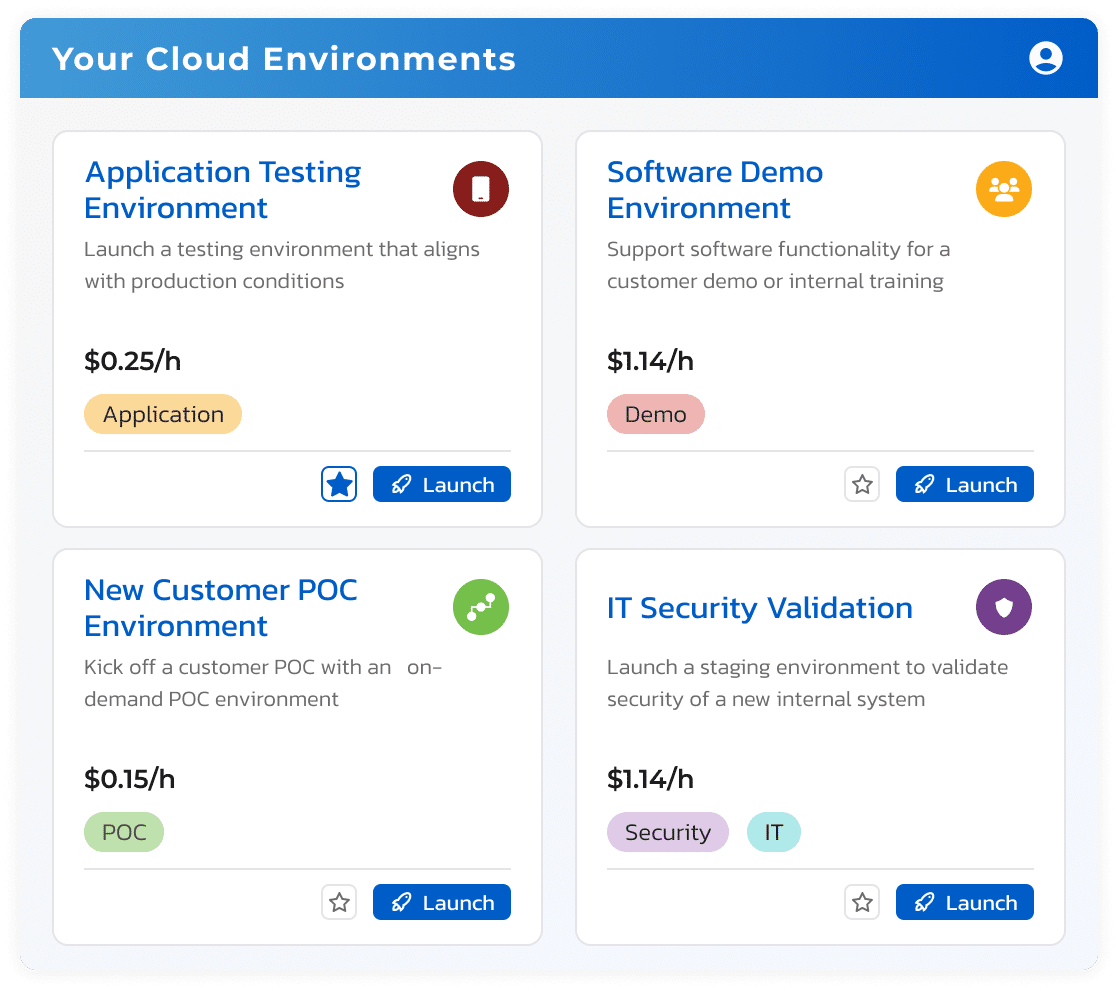
Accelerate developer productivity with reusable templates for your unique application environments. Quali Torque creates a developer platform to launch environments for software development, testing, demos, and any other use case based on pre-configured templates that leverage your existing Infrastructure as Code and Kubernetes resources.